Tag: security
-
Vanessa and the Law
Once, Vanessa was given an “enhanced security” screening for having a hair tie in her back pocket. You better believe I’m never going to forget that. “Don’t forget to check your pockets for lint!” Also on: Twitter Twitter
-

Two Factor Authentication with Jetpack
Over the summer, I wrote up a quick one-file plugin to force site administrators to use Jetpack’s Single Sign-On via WordPress.com, specifically with two-factor authentication1. It was closed-sourced initially, for no other reason than it was experimental and didn’t want to make a promise it was coming without it being proven. Without further ado, I…
-
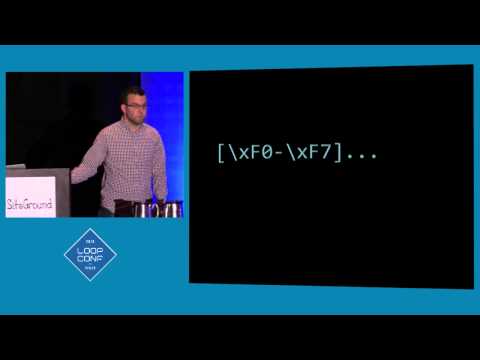
How Emoji Saved Your Site’s Hide
Emoji was a front for four-byte support which was a front for a major security improvement.